Posted by Anne-Marie Avalon
February 16, 2024
In the aftermath of the Cloudflare breach, triggered by previously compromised credentials from an Okta incident, a critical operational challenge came to light: the monumental task of secrets rotation. Despite Cloudflare’s cognizance of the October Okta breach, the sheer complexity and scale of rotating all exposed credentials proved to be a daunting endeavor. This challenge underscores a pivotal aspect of cybersecurity—the intricate, often cumbersome process of secrets management and rotation, even for an organization as technologically adept as Cloudflare.
The Critical Practice of Secrets Rotation: A Recap of the Cloudflare Breach
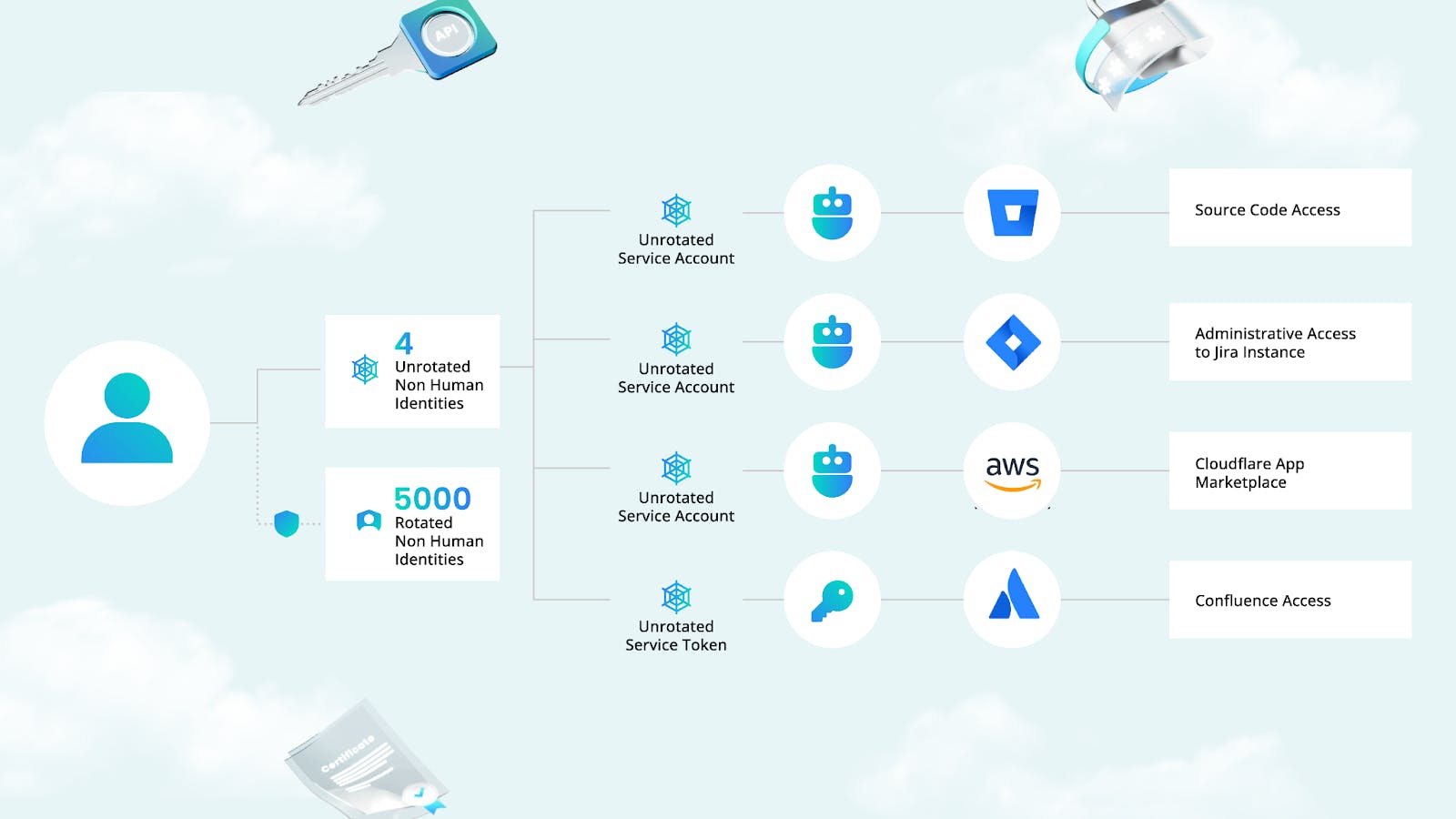
On November 14, Cloudflare’s self-hosted Atlassian server was breached by what were suspected to be nation-state hackers, utilizing an access token and three service account credentials that had been compromised in an earlier Okta breach but had not been revoked by Cloudflare. The breach affected Cloudflare’s Confluence, Jira, and Bitbucket systems but failed to penetrate the company’s São Paulo data center, which was not yet operational. The attackers managed to establish persistent access, aiming for deeper network infiltration.
By November 23, Cloudflare had detected the breach, quickly moving to sever attacker access by the next morning. The response strategy included rotating all 5,000 production credentials, segmenting test and staging systems, conducting an extensive forensic investigation, and rebooting all company systems.
This incident highlights not only the necessity of secrets rotation but also the importance of rapid intrusion detection to prevent or mitigate similar breaches.

Learn More: Auto-Rotating Credentials: Safeguarding Legacy and Bare Metal
Operational Complexities and Response Challenges
Following the discovery of the breach, Cloudflare was thrust into an extensive and labor-intensive process to secure their systems. The task at hand was immense; it involved rotating all production secrets, a critical step to sever the attackers’ access and mitigate further risks. This intricate process required a thorough analysis of all testing and development environments and even the return of data center hardware to vendors for comprehensive analysis. The endeavor stretched into January, highlighting the substantial time and effort required to fully address and rectify the breach’s implications.
The difficulty faced by Cloudflare in rotating thousands of secrets post-breach underscores the need for automated systems that can facilitate this crucial security measure more efficiently. Manual secrets management processes are increasingly untenable in the face of sophisticated and agile cyber threats.
The Importance of Streamlined Secrets Management
Effective secrets management not only involves the secure storage and access of sensitive credentials but also the capability for rapid rotation in the event of a compromise. Cloudflare’s challenge in rotating many secrets highlights the need for automation. Automated systems speed up this crucial security step, lessening cyber threat impacts.
The Importance of Frequent Rotation Through Automation
The frequency of secrets rotation is a critical factor in security efficacy. Storing rotated secrets in configuration files or repositories without frequent updates can still pose a risk, as exposed credentials might be exploited within their rotation window. Akeyless addresses this by enabling more frequent, automated rotation, which minimizes the risk associated with stale credentials.
Introducing the Akeyless Platform for Simplified Secrets Management
Akeyless offers a Vaultess SaaS Secrets Management platform designed to address the operational complexities associated with secrets management and rotation. By automating these processes, Akeyless not only alleviates the burden on IT teams but also significantly reduces the time window during which attackers can exploit compromised credentials.
Automating Security Resilience with Akeyless
Akeyless approach goes beyond mere automation of secrets rotation. It provides a comprehensive secrets management ecosystem, integrating secure storage, access controls, and real-time monitoring to detect unusual access patterns. This integrated approach ensures seamless protection across cloud, hybrid, and on-premises environments, addressing the modern digital landscape where traditional security perimeters no longer exist.
Leveraging Akeyless for Automated Secrets Rotation
The platform’s automated secrets rotation feature is designed to replace secrets at predetermined intervals, aligning with security standards like PCI DSS, which mandates a rotation cycle of up to 90 days. This feature is particularly crucial for high-risk accounts and databases, where rotated secrets can significantly mitigate the risk of credential compromise.
However, implementing rotated secrets can present challenges. Manual rotation processes are resource-intensive and require meticulous logging for audit purposes, adding another layer of operational complexity. Akeyless automation capabilities simplify these processes, ensuring that rotated secrets are frequently updated without manual intervention, thereby enhancing security without adding operational burden.
A Blueprint for Future Cybersecurity Strategies
The Cloudflare incident is a cautionary tale that underscores the importance of advanced secrets management solutions in contemporary cybersecurity strategies. The integration of automated, intelligent secrets management systems, such as Akeyless, is crucial for building a secure, resilient digital infrastructure capable of repelling sophisticated cyber threats.
Organizations must recognize the role of secrets management as a cornerstone of digital security strategy. Adopting solutions like Akeyless not only enhances security postures but also equips organizations with the agility needed to respond swiftly to emerging threats.
Learn more: How the LastPass Breach Highlights the Importance of Secrets Management
Lessons Learned and Moving Forward
The Cloudflare breach stemmed from a failure to rotate secrets, crucial in cybersecurity. Secrets rotation is key for security. It changes credentials and tokens periodically. Yet, managing many secrets is complex and daunting. This is especially true for large organizations.
The Akeyless Platform marks progress in secrets management. It automates rotation and simplifies management. This tackles operational challenges directly. Akeyless narrows opportunities for attackers, boosting security. The platform streamlines information management. It also ensures regular credential updates.
Don’t let your organization suffer a breach. Use Akeyless to strengthen your defenses. It offers automated rotation and efficient management. This approach reduces vulnerabilities and anticipates threats.
Contact us for details on securing and managing your secrets with Vaultless® Secrets Management.












