Posted by Miryam Brand
May 27, 2022
Adversaries have many devious ways to get access to an organization’s data, for different reasons, including data theft or ransom. Many of their actions can be categorized in different steps as part of a concept known in cyber security as a kill chain. Meanwhile, security teams are looking for ways to break this chain, and the way organizations manage their access and their secrets, proves to be a powerful weapon against adversaries.
Kill Chain Breakdown
The cyber kill chain explains the sequence of events that are involved in an external attack on an organization’s IT infrastructure. Breaking down the attack process in a chain model helps security teams put strategies and technologies in place to contain the attack at various stages, to mitigate the scale and impact of a breach.
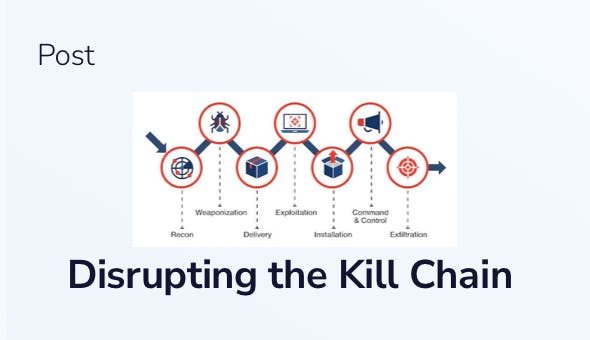
The cyber kill chain concept was initially developed by Lockheed Martin. The term “kill chain” is used to break down the structure of a military attack into distinct, sequential stages:
- Reconnaissance
The attacker researches their intended target and looks for vulnerabilities. - Weaponization
The attacker develops malware designed to exploit the vulnerability.
- Delivery
The attacker transmits the malware, for example by using a phishing email, or a sufficient-privilege access option. - Exploitation
The malware is executed on the target system.
- Installation
The malware installs a backdoor or other ingress accessible to the attacker. - Command and Control
The intruder gains persistent access to the victim’s systems/network.
- Actions on Objective
Intruder initiates end goal actions, such as data theft, data corruption, or data destruction.
Kill Chain in the New World
Since the creation of Lockheed Martin’s concept, a lot has changed. The classic perimeter concept, where everything outside the corporate network is “unsafe”, and everything inside the firewall is “safe”, is increasingly considered to be obsolete. Identity is now the new perimeter, and Zero Trust concepts dictate more due diligence with verifying identities, roles, and policies before connections are allowed to be established.
Secrets vs. Kill Chain
The use of secrets (i.e. credentials, certificates, and keys), has proliferated due to DevOps, Hybrid Multicloud, and automation trends such as containerization as well as the use of microservices. Secrets are used to authenticate user and machine identities. Secrets’ safekeeping is vital to an organization’s security posture. Attackers use stolen credentials 80% of the time to gain initial access to infrastructure, and then to move laterally and/or escalate their privileges and reach their goal of accessing sensitive data.
Static Secrets
Classic credentials, or static secrets, are usually active for months, often significantly longer than needed. They are also rarely updated, if ever. This provides attackers with a large window of opportunity to deploy their kill chain. Secrets are also often found in source code, scripts, and logs. This phenomenon of static secret sprawl is both a security risk and a logistical and administrative nightmare.
Dynamic Secrets
Mitigating the risk of leaked static secrets is to eliminate standing permissions. Dynamic secrets are temporary credentials that are generated on-demand to provide a client with access to a resource for a limited period (only as long as needed) and with a least privilege permission profile. By doing so, even if a secret leaks, it effectively becomes useless before it can be abused.
In short, with dynamic secrets, clients get access to a resource with the minimum privileges they need to accomplish a specific task, for the minimum time required. Dynamic secrets are also known as “just-in-time” (JIT) credentials, a term borrowed from the manufacturing industry where materials are ordered only when needed, to improve efficiency.
A sample scenario of dynamic secrets is when an app needs to access a datastore on AWS. The app requests the credentials from a centrally available secrets management solution, acting as a dynamic secrets vault. In turn, the vault generates a credential with the appropriate permissions for that client’s role. After the credential time-to-live (TTL) expires, which could be just a few seconds for ephemeral machine-to-machine operations, the vault revokes the account. The dynamic secret could be valid for longer time periods for human or machine access purposes, as needed.
Conclusion
Similar to how the classic perimeter concept evolved over time to focus on identities, so will our use of secrets. By virtually eliminating the long time window an attacker gets with compromised static secrets, dynamic secrets severely limit an attacker’s ability to maintain access and deploy the kill chain.
The Akeyless Vaultless® Platform enables organizations to easily migrate to a Just-in-Time access environment with a unified, SaaS-based solution for Secrets Management, Secure Remote Access, and Data Protection. The Akeyless Vaultless® Platform is SOC2 and FIPS certified and operates across a highly distributed environment, delivering Just-in-Time secrets and access to users and machines (i.e., applications, microservices) efficiently and at infinite scale.