Posted by Miryam Brand
July 18, 2022
The landscape of cybersecurity is continuously evolving. In this digital age where data is the new gold, the quest for secure privileged access is paramount. The dawn of static secrets, including credentials, certificates, and keys, has given rise to an innovative solution – Just-in-Time (JIT) Secrets Management. This approach has emerged as a game-changer in mitigating risks associated with compromised secrets. Read on to learn how Just-In-Time secrets help secure software supply chains.
The Pitfalls of Traditional Secrets Management
Traditionally, secrets management has been static, presenting a plethora of security risks. Static secrets, if not regularly rotated or updated, leave a wide window of opportunity open for adversaries. This prolonged vulnerability can lead to unauthorized access, catastrophic data breaches, and compromised systems.
Deploying a robust Secrets Management solution can significantly mitigate these risks. Such a system automates the frequent rotation of secrets, shortening their lifecycle. Moreover, these rotations can occur seamlessly, without disrupting the workflow of the identities employing these secrets.
Just-in-Time Secrets Management Helping to Secure Software Supply Chains
Building on the foundations of traditional secrets management is the concept of Just-in-Time (JIT) Secrets Management. Borrowed from the manufacturing industry, JIT is an efficiency-driven approach where materials are procured only when needed, thereby enhancing efficiency and reducing waste.
In the realm of Secrets Management, JIT brings a similar shift. Rather than relying on long-standing static secrets, JIT employs dynamic secrets. These are generated on-demand for identities (be it human users or machine identities), endowed with the bare minimum privileges they require for a specific task. Importantly, these secrets are transient, lasting only for the shortest possible time necessary – typically, just a few seconds or minutes.
Unpacking the Value of Just-in-Time Secrets
JIT ushers in several benefits in the field of Secrets Management. Firstly, dynamic secrets significantly truncate the window of vulnerability as they expire almost immediately after use. This limited lifespan means that a compromised secret is almost instantly useless to an attacker, mitigating potential threats.
Secondly, JIT reinforces the principle of least privilege. This approach ensures that identities receive only the bare minimum permissions needed for a task, thus minimizing the risk of over-privileged access leading to potential misuse or exploitation.
Furthermore, the on-demand nature of JIT secrets reduces the overhead of managing and storing long-term secrets. This enhanced efficiency can have significant implications for resource allocation and operational overhead, especially in large-scale organizations.
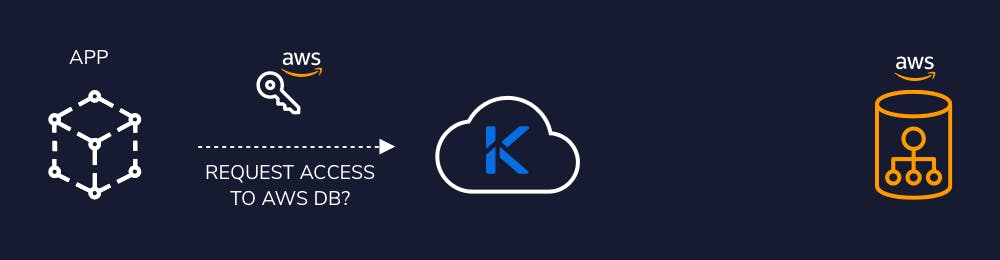


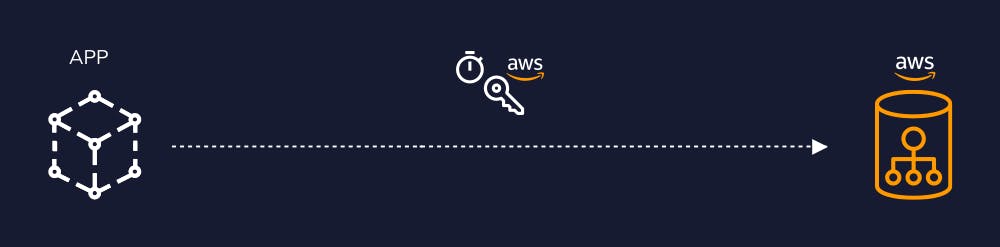
Akeyless: Your Ally in Just-in-Time Secrets Management
Leading this transformative journey is Akeyless, offering a suite of solutions to facilitate the adoption of JIT secrets management. By supporting automated rotation mechanisms and JIT access scenarios, Akeyless significantly curtails the risk of leaked or compromised secrets.
Akeyless provides JIT access for various targets out-of-the-box, such as:
- Databases like MySQL, PostgreSQL, Mongo DB, Snowflake, among others
- Cloud Platforms (Azure, AWS, GCP)
- GitHub
- Kubernetes
- Chef
For each use-case, Akeyless crafts a solution tailored to the specific requirements of the application, guaranteeing optimal efficiency and security.
The Future is Just-in-Time
The paradigm shift from static to dynamic, Just-in-Time secrets marks a significant advancement in Secrets Management. By curtailing the lifespan of secrets, enforcing least privilege, and offering on-demand access, JIT provides a potent strategy to address the vulnerabilities inherent in traditional static secrets.
As we navigate the evolving digital terrain, the demand for secure, efficient, and dynamic Secrets Management has never been more critical. Akeyless, as your strategic partner, ensures your transition towards JIT Secrets Management is both smooth and effective.
Embark on your journey towards a safer digital future. Book a demo with Akeyless to understand how easy it is to transition from the risks of static secrets to the robust security of Just-in-Time Secrets Management. A more secure future is just a click away.
















