Posted by Miryam Brand
June 23, 2022
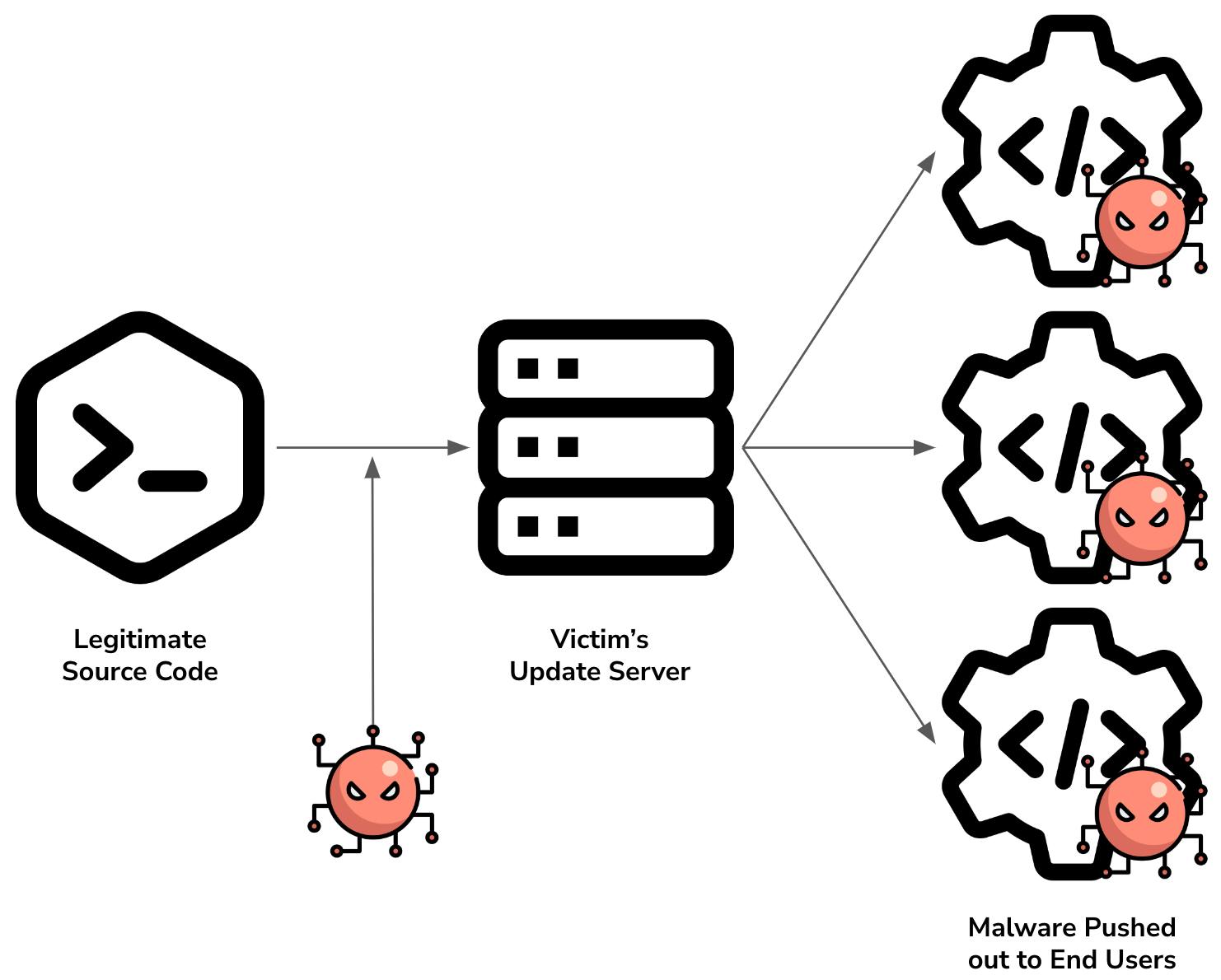
A software supply chain attack is a cyber attack where less secure elements in the chain such as third-party networks or code repositories are compromised by attackers as a means to embed hidden malware, which then finds its way into the infrastructures of organizations that use the final software.
In these attacks, attackers try to compromise source code, build processes or update mechanisms and install malware that steals data, initiates malicious activity, or allows further breaches down the supply chain, such as when a customer installs the final software.
Software products consist of many components, which are often supplied by other vendors or programmers and are stored in different repositories. Once they have a way in, attackers embed the malware and ensure the sub-component is signed, so it is inherently trusted once it makes its way through the supply chain.
High-Risk Ingredients of The Software Supply Chain
Attackers always try to leverage the weakest link in the chain to gain access and embed malware. This weakest link may be smaller companies with fewer and less rigorous preventive security measures, especially if parts of their code can be found in public repositories.
One of the most popular ways for an attacker to get an “in”, is to leverage leaked secrets – that is, keys, certificates, or credentials. Unfortunately, there are many very recent examples where secrets such as OAuth tokens are exposed, providing attackers with ample opportunity to find a way into a code repository and embed malicious code.
One of the main reasons that these secrets keep getting exposed is that Secret Sprawl is a prevalent issue: developers frequently embed secrets into code or configuration files found in numerous locations. Often developers do this because they are under time pressure and want to find the shortest path to a working solution. Sometimes these leaks occur because the tools developers use do not provide adequate protection for securely storing secrets, or because these secrets are easily found in the solution’s log files. When secrets are stored in plain text, a strong or complex password does not offer any additional protection.
One additional problem is the use of long-standing privileges, also known as static secrets. Frequently, these static secrets are not periodically refreshed, or rotated, to limit and shorten the secret’s lifecycle. In these cases, it is only a matter of time before an attacker either guesses, steals, or buys a valid secret, and then has a long time to try and gain unauthorized access to code repositories and compromise the code with malware.
Curb Supply Chain Risk with Secrets Management
Solving a complex problem like supply chain risk begins with addressing the largest problem first. Secret Sprawl is still a major cause of secrets exposure and an increasingly critical concern for security teams. A secrets management solution includes an encrypted vault which keeps credentials and keys secure, an essential element for stopping the sprawl and preventing supply chain hacks.
Ideally, a secrets management solution will also provide developers with simplified workflows for their code to access secrets as needed, regulated by policies that are approved by the security team. Security teams can define the correct policies for securing keys and credentials while allowing developers to easily create the applications they need.
To curb the danger of leaked credentials and keys, the ideal secrets management solution must also be able to easily rotate secrets so that if a leak does occur it is rendered ineffectual. The best solution for this are dynamic or “Just-in-Time” secrets, which are created anew for each connection and immediately expire. If hacked, these secrets cannot be used – they have already expired.
The Akeyless Vaultless Platform
The Akeyless Vaultless Platform provides a centralized Secrets Management solution that allows organizations with a hybrid or multicloud infrastructure to securely store their secrets in an encrypted vault. The Akeyless patented DFC™ technology is the backbone of a Zero Knowledge solution, so that not even Akeyless has access to the organization’s full encryption keys.
To prevent supply chain hacks, Akeyless makes it easy to automate and apply high-frequency secret rotation mechanisms. A centralized vault allows security teams to see and control how secrets are used so that alerts can be triggered by any unusual behavior.
As mentioned above, long-standing privileges are an attacker’s best friend. If a secret leaks, attackers have time to abuse this valid access method until the secret is rotated. To curb the risk of long-standing privileges and move beyond regular secret rotation, Akeyless provides Just-in-Time (JIT) access. With JIT access, authorized identities get access to their required target through a credential that has been created on-demand, and provides the least level of privileges for the connecting identity to perform its role. The secret is only valid for a limited time (minutes or seconds) and is automatically revoked once the session expires. This revolutionizes the connection process for human-to-machine (H2M) communications and especially for machine-to-machine (M2M) communications. JIT drastically reduces the risk of secret leaks that result in software supply chain attacks.
To learn more about how Akeyless elevates security in hybrid multicloud organizations and easily integrates into DevOps workflows, book a demo.
















