Posted by Sam Gabrail
October 2, 2024
Introduction
As organizations adopt hybrid cloud environments, secrets management has become critical to security and operational efficiency. Organizations often grapple with handling sensitive data like API keys, certificates, passwords, and other credentials. As the number of secrets grows, so does the risk associated with managing them improperly, including the need to securely store encrypted data.
Imagine, as a platform engineer, you want to centralize secrets management with one secrets manager tool. However, your development teams are tied to specific options like AWS Secrets Manager or Google Secret Manager due to cloud-native requirements or unique use cases. Akeyless Universal Secrets Connector (USC) unites all your secrets managers, solving the chaos with a single access point—without forcing migration. In this article we will see USC in action.
A Demo Video
Dangers of Secrets Sprawl Across Multiple Secrets Management Tools
Increased Security Risks
When secrets are dispersed across multiple tools like HashiCorp Vault, Azure Key Vault, and AWS Secrets Manager, maintaining consistent security policies becomes a daunting task. This fragmentation can lead to potential vulnerabilities and unauthorized access, as inconsistencies in security measures are more likely to occur. Additionally, detailed audit logs are essential for tracking access to secrets and ensuring accountability, making it easier to monitor who is accessing which secrets. Using multiple tools prevents the ability to log and monitor secret access centrally.
Complexity and Management Overhead
Managing secrets across different platforms creates significant administrative burdens. The complexity increases the likelihood of misconfigurations and errors, which can compromise the overall security posture. Administrators may struggle to keep track of where secrets are stored and how they are secured, making it difficult to tightly control access across disparate systems.
Reduced Visibility and Control
Secret sprawl results in fragmented oversight, making it difficult to monitor, audit, and ensure compliance. This lack of visibility elevates the risk of data breaches and compliance violations, as organizations cannot effectively enforce policies or respond quickly to security incidents. A robust and unified secrets management tool can revoke not only single secrets but also entire trees of secrets to enhance security.
Balancing Security with Developer Productivity
Striking the right balance between stringent security measures and developer productivity is essential. Overly restrictive access controls can hinder developers, slowing down innovation and deployment. On the other hand, lax controls can open the door to security breaches.
Effective secrets management requires policies that protect sensitive data by providing tight access control without impeding the workflow of development teams. Achieving this balance ensures that security protocols are robust yet flexible enough to accommodate the needs of the organization.
Best Practices for Managing Secrets
Secure Your Credentials and Certificates
Sensitive data such as API keys and certificates must be stored securely. Utilizing encrypted storage solutions and implementing strong encryption algorithms are fundamental practices. Access to these secrets should be tightly controlled and monitored.
Implementing a centralized secrets management tool is crucial in achieving these objectives. A central platform like Akeyless Universal Secrets Connector (USC) ensures that all credentials and certificates are stored in a secure, encrypted environment. It provides a unified interface for managing secrets, allowing organizations to enforce consistent security policies, tightly control access, and monitor usage across all platforms and environments.
Manage Secrets Across the Enterprise
Consistency in access controls and encryption across all environments and systems is crucial. A centralized approach ensures that policies are uniformly applied, reducing the risk of gaps in security. Enterprise-wide management facilitates easier auditing and compliance with regulations.
Introducing Akeyless Universal Secrets Connector (USC)
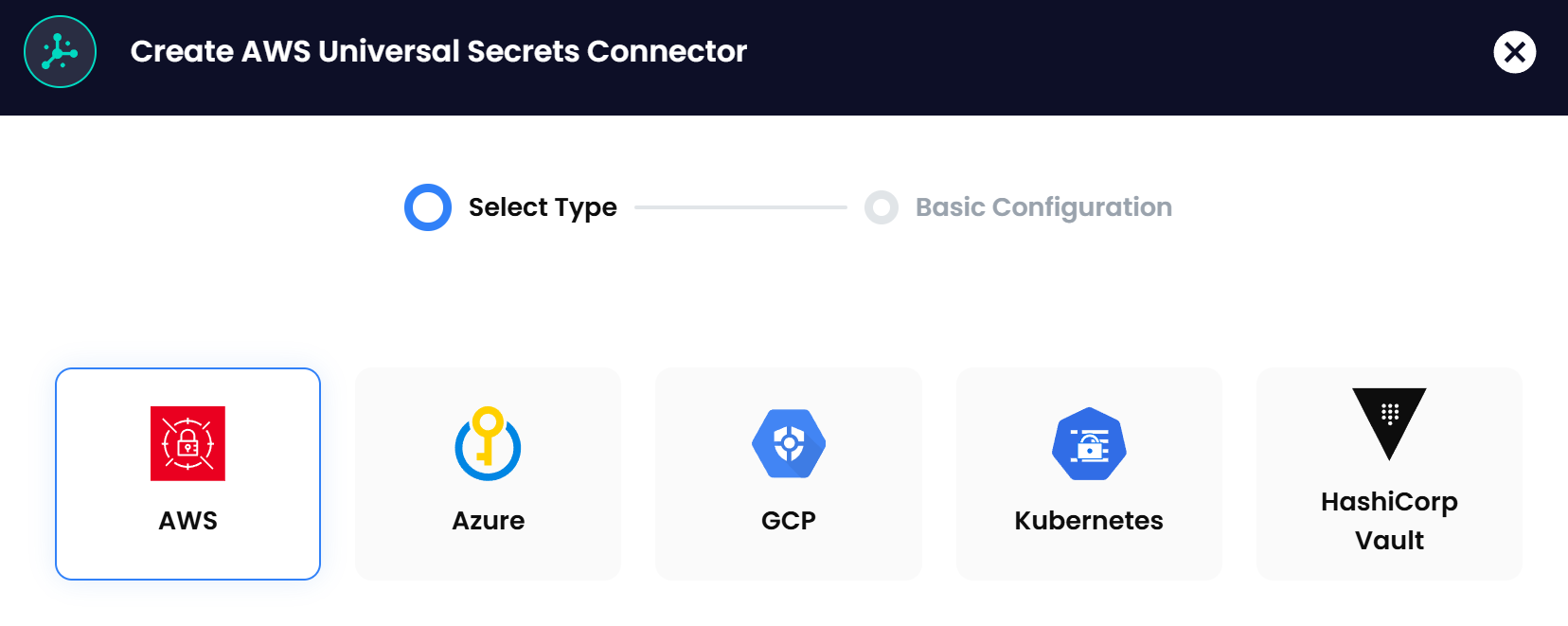
Akeyless USC provides a centralized platform for managing secrets across various cloud providers and platforms. It integrates seamlessly with AWS Secrets Manager, Google Secrets Manager, Azure Key Vault, Kubernetes, and HashiCorp Vault.
Centralized Management Across Platforms
With Akeyless USC, organizations gain a unified interface to manage secrets, eliminating the need to navigate multiple tools. This centralization simplifies administration and enhances security by providing consistent policies and controls.
No Migration Needed
One of the standout features of Akeyless USC is the ability to manage secrets without migrating them to a new system. Organizations can continue using their existing secrets managers while benefiting from centralized oversight.
Enhanced Security and Compliance
Akeyless USC offers centralized logging, monitoring, and auditing capabilities. This consolidation supports compliance efforts and provides better visibility into how secrets are accessed and used across the organization.
Simplified Authentication
By providing a single authentication point for multiple secret managers, Akeyless USC simplifies access control. Users can authenticate once to gain access to all authorized secrets, streamlining workflows and improving productivity.
Demo: Highlighting the Akeyless Universal Secrets Connector
Objective
In this section, we’ll demonstrate how Akeyless USC manages secrets across multiple platforms, enhances security, and simplifies authentication and access control. We have three examples to show below.
1. AWS Secrets Manager Sync with USC
In the Akeyless console, you can create Universal Secrets Connectors for different platforms. Let’s start with AWS. By configuring a connector for AWS Secrets Manager, you can view and manage your AWS secrets directly from Akeyless. Below is the view from Akeyless:
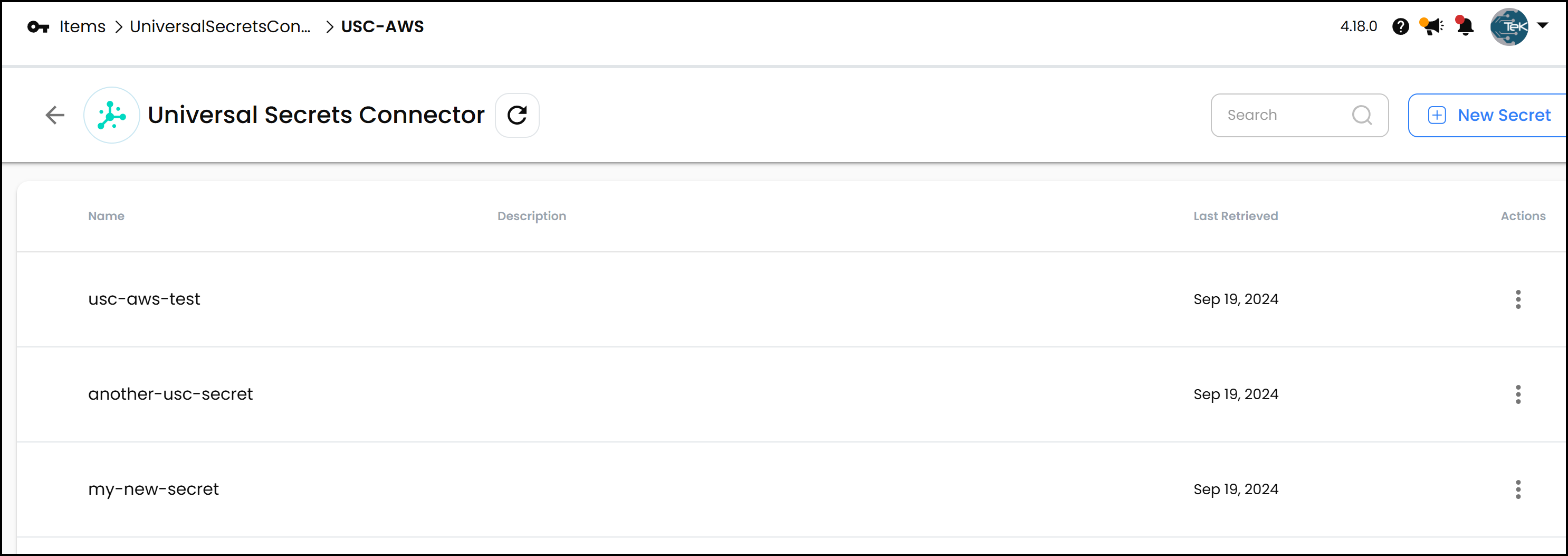
For example, I have three secrets shown above in AWS Secrets Manager. These will appear in the Akeyless interface. You can view, edit, or delete these secrets from Akeyless, and any changes will sync with AWS. This is shown in the demo video at the top of this post.
Adding a new secret is seamless. If you create a new secret in AWS Secrets Manager—let’s say my_new_secret with a key-value pair of new_key: new_value—it will automatically appear in Akeyless after a refresh. This synchronization ensures that your secrets are consistent across platforms.
Below is the view in the AWS Console:
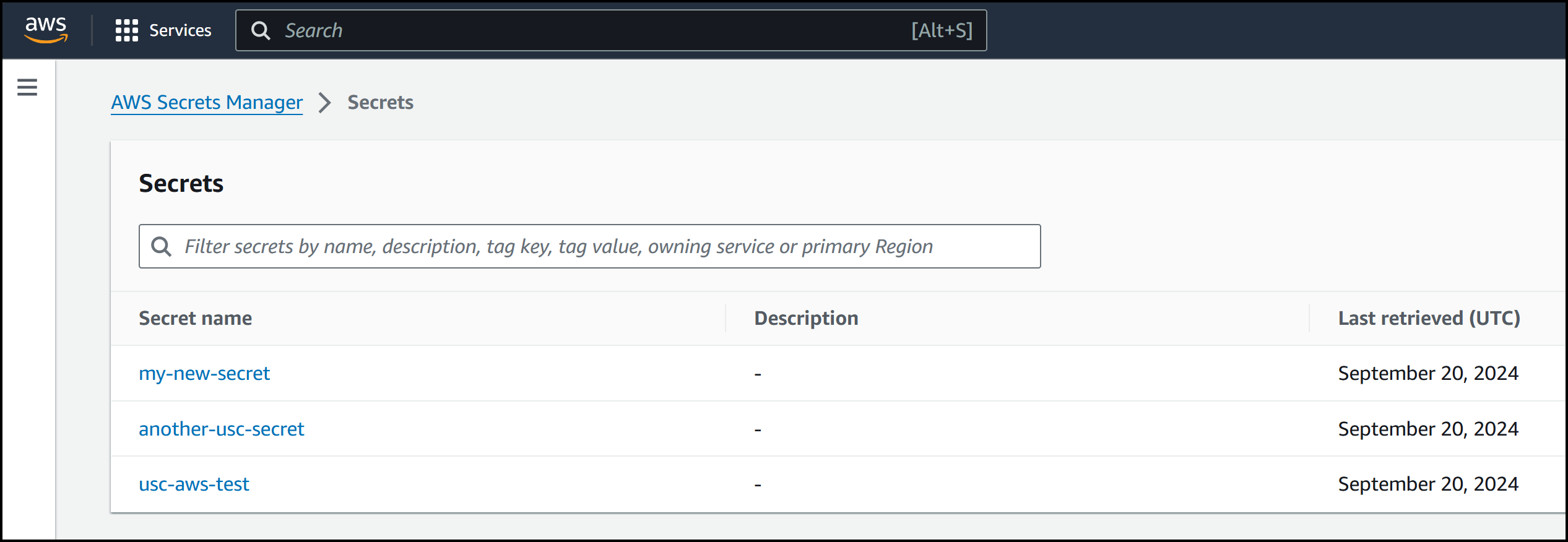
2. HashiCorp Vault Sync with USC
Similarly, you can connect Akeyless USC to HashiCorp Vault. After setting up the connector, all your Vault secrets become accessible through the Akeyless interface. Below is the view in Akeyless:
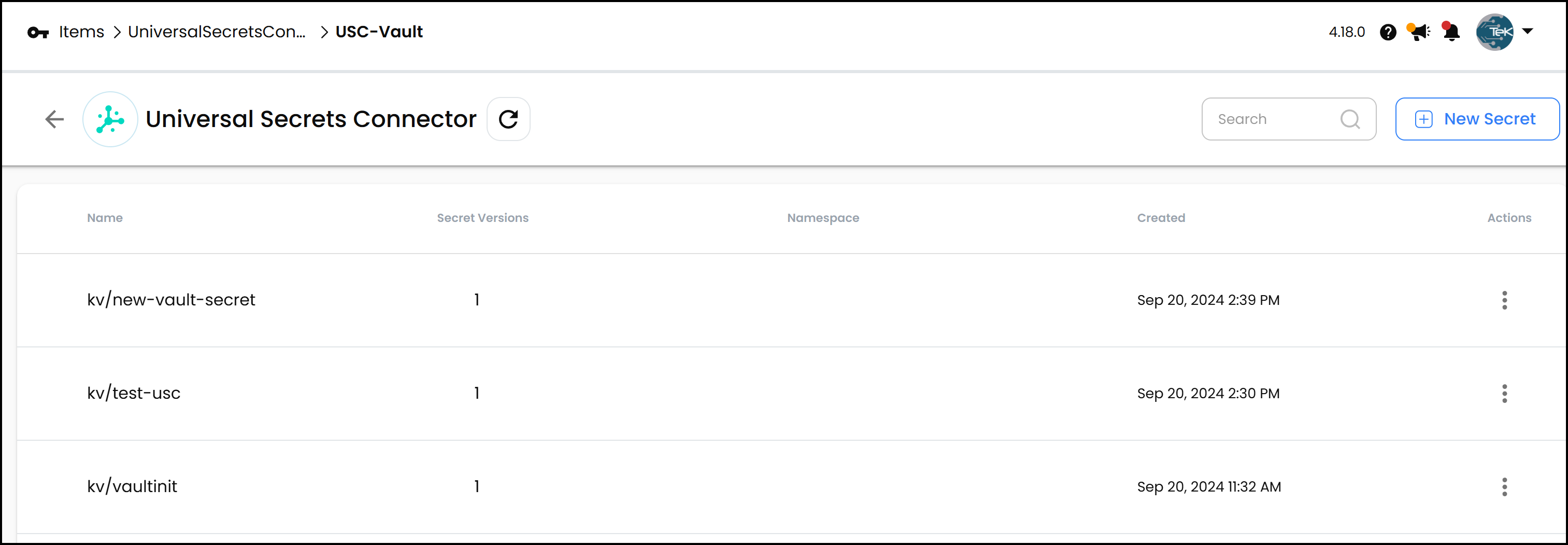
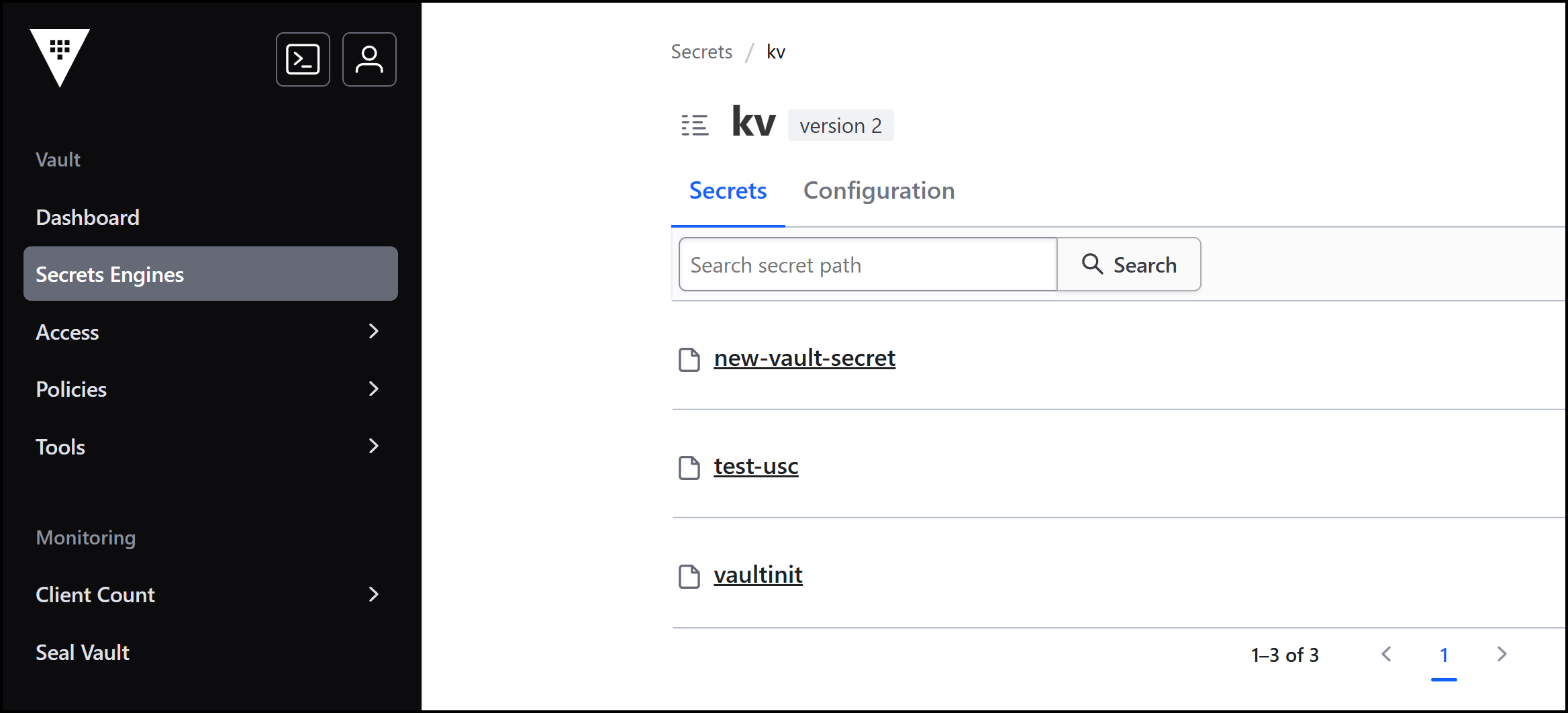
We have a few secrets in HashiCorp Vault that are synced to Akeyless. If you add a new secret in Akeyless—let’s call it new_vault_secret with content foo: bar—it will appear in Vault instantly. Notice this time we created the secret in Akeyless as opposed to the first example where we created the secret first in AWS. This bidirectional sync keeps your secrets up-to-date, no matter where you manage them. Below is an image of the secrets in Vault:
3. Kubernetes Secrets Sync with USC
Akeyless USC also supports Kubernetes secrets. By configuring a connector to your Kubernetes cluster, you can manage secrets stored in Kubernetes directly from Akeyless.
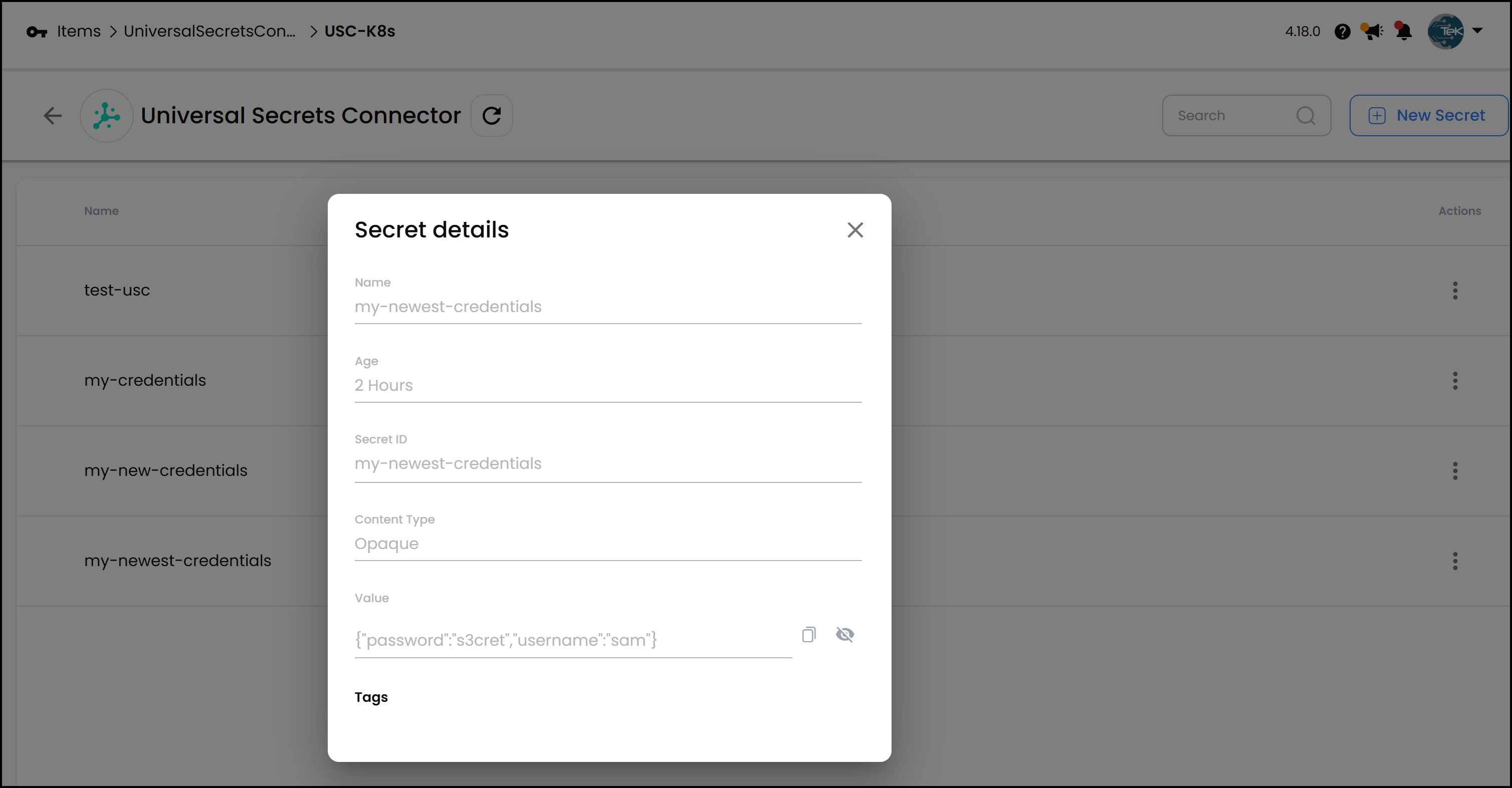
For instance, if you have a secret named test_usc in the default namespace of your Kubernetes cluster, you can view and edit it from Akeyless. If you create a new secret in Kubernetes—say my_newest_credentials with data username: sam and password: se3cret—it will show up in Akeyless as shown above.
You can also see the secret in Kubernetes as shown below.
$ kubectl get secrets
NAME TYPE DATA AGE
test-usc Opaque 1 177m
my-credentials Opaque 2 174m
my-new-credentials Opaque 2 164m
my-newest-credentials Opaque 2 157mand the my-newest-credentials:
$ kubectl get secrets my-newest-credentials -ojson | jq -r '.data.username' | base64 --decode
sam
$ kubectl get secrets my-newest-credentials -ojson | jq -r '.data.password' | base64 --decode
s3cretConfiguring Universal Secrets Connector
Setting up connectors in Akeyless is straightforward. When adding a new Universal Secrets Connector, you select the platform (e.g., AWS, Kubernetes, HashiCorp Vault) and provide the necessary details.
Each connector requires a target, which is the endpoint of the secrets manager you’re connecting to. For example, connecting to HashiCorp Vault requires specifying the Vault’s URL and authentication token.

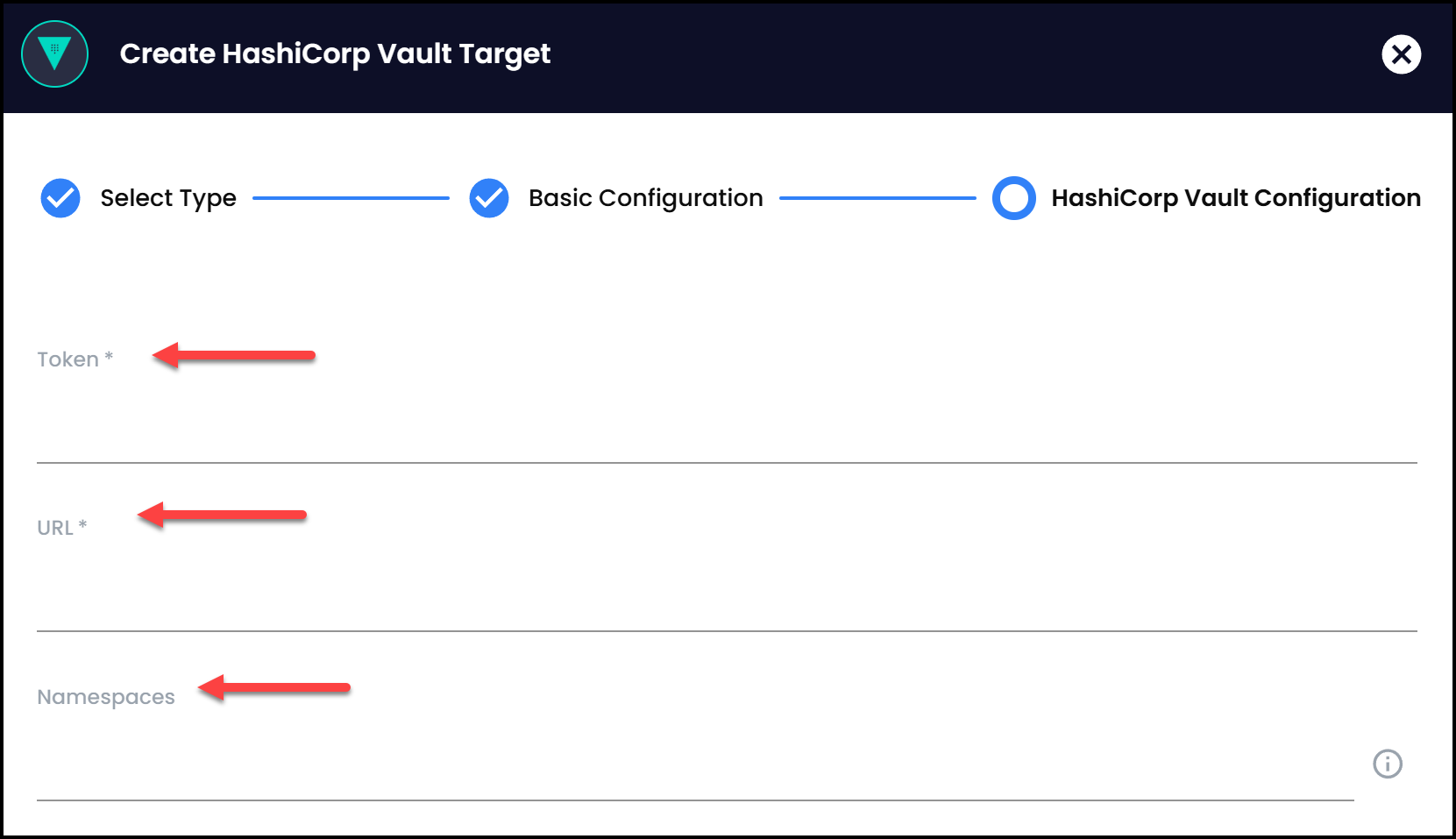
Similarly, connecting to Kubernetes may involve using a service account or bearer token.
Setting Up Targets
Before configuring connectors, you need to define targets in Akeyless. Targets are the connection details that allow Akeyless to communicate with your secrets managers.
- HashiCorp Vault: Create a target by specifying the Vault URL and a token for authentication.
- Kubernetes: Use a gateway service account, a service account bearer token, or client certificate to authenticate.
- AWS: Provide access keys to connect to AWS.
- Azure and GCP: Similar configurations apply, requiring credentials and endpoints.
Once targets are set up, they can be used by the Universal Secrets Connectors to manage secrets across platforms.
Conclusion and Final Thoughts
Akeyless Universal Secrets Connector acts as a manager of managers for all your secrets managers. It addresses scenarios where teams need to use native secrets managers due to specific requirements while still providing centralized management and oversight.
By unifying access to AWS Secrets Manager, Google Secrets Manager, Azure Key Vault, Kubernetes, and HashiCorp Vault, Akeyless USC simplifies secrets management, enhances security, and boosts productivity. There’s no need for complex migrations or disruptions to your existing workflows.
I encourage you to explore Akeyless Universal Secrets Connector for your secrets management needs.
















