Secretless Developer Access
Remove friction for developers while maintaining Zero Trust security
Apply security best practices and allow your developers to access sensitive infrastructure without secrets.
- Easily implement Zero Trust without slowing down your developers
- Eradicate standing privileges to reinforce your organization’s security
- Make audit season easy with recordings and logs of every session
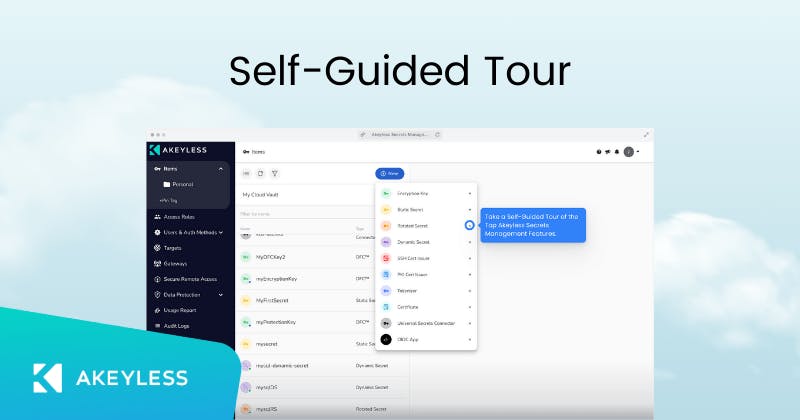
Features
- Enable Just-in-Time access for all sensitive systems
- Integration with Identity Providers for easy authentication
- Create a Zero Trust environment with no standing privileges
- Enable recordings of all access sessions for compliance and security
- Implement security policy across the organization via role-based access control
-
Integrations
The Akeyless platform includes out-of-the-box integrations with all the tools your team uses on a daily basis
-
Auditing and Compliance
Akeyless puts security and compliance with international standards at the heart of our service
-
Unique Technology
Akeyless is built on a patented technology that ensures our customers’ data is always secure and encrypted