
With fragmented and dynamic encryption distributed across multiple regions and cloud providers, your keys are never in a single location or static state, restricting an attacker from gaining access via a single attack vector.
Akeyless NIST FIPS 140-2 validated cryptography technology enables Zero-Knowledge encryption with full ownership over your secrets.
DFC delivers a revolutionary way to conduct cryptography operations with auto-scalability, anytime/anywhere access, and exclusive ownership
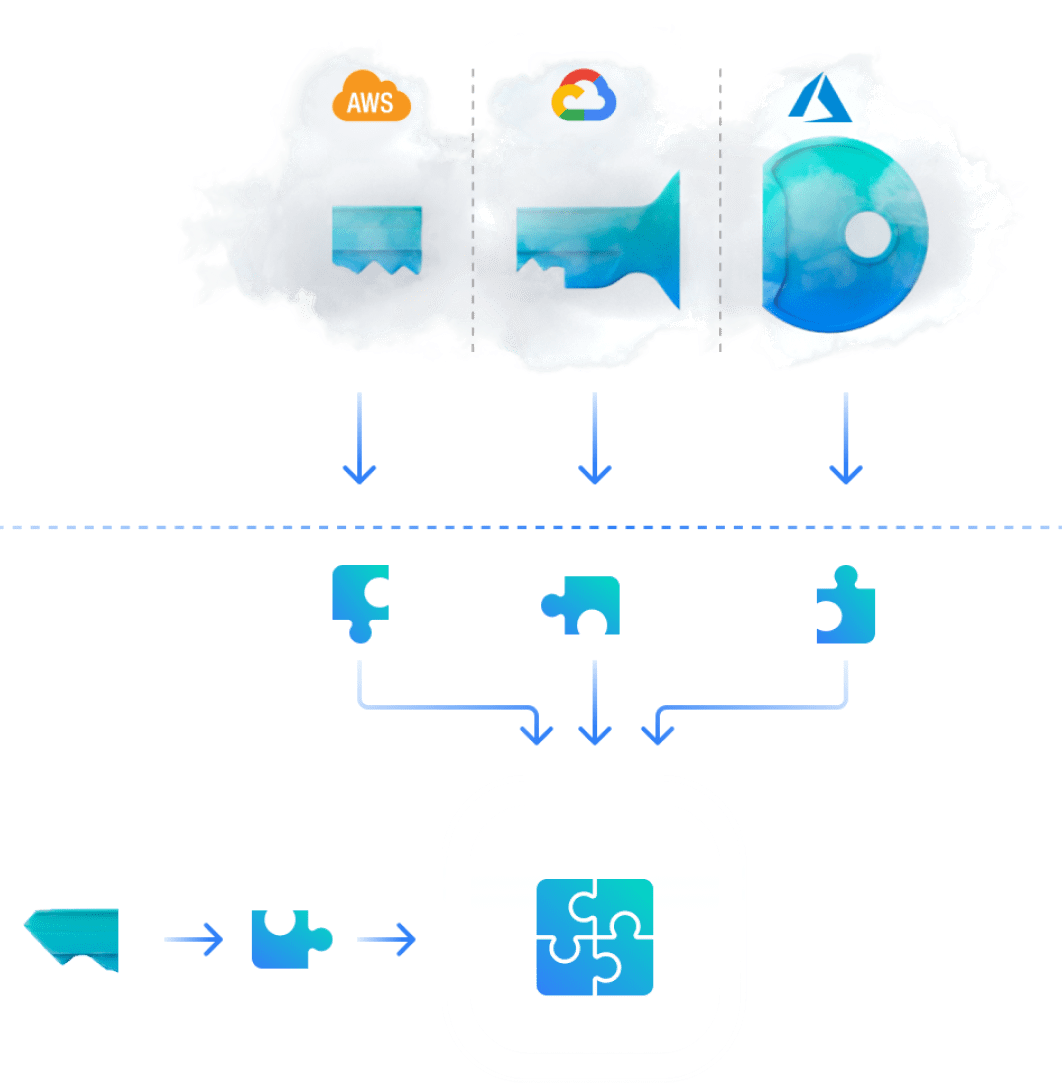
Our patented technology performs cryptographic operations using fragments of an encryption key that reside across different regions and cloud providers. These fragments function as separate keys that are never combined, not even during the encryption or decryption process.
One of the fragments is created and kept in your environment, which only you have access to. This ensures you maintain exclusive ownership while Akeyless has Zero Knowledge of your keys.
Akeyless DFC™ adds an additional security layer through the key fragments constantly refreshing their mathematical values. These values dynamically change without breaking their overall sum.
An attacker would need to penetrate three separate cloud service providers as well as the customer’s environment to access the different fragments at the exact same time. This means your secrets are almost impossible to hack.

With fragmented and dynamic encryption distributed across multiple regions and cloud providers, your keys are never in a single location or static state, restricting an attacker from gaining access via a single attack vector.

Maintaining your own key fragment means only you can access your keys, protecting them from unauthorized access from CSPs, malicious attackers, federal authorities or others.

DFC™ enables our lightweight, vaultless SaaS solution. Instead of contending with complex, burdensome vaulted solutions, you can easily deploy, maintain, and scale while maintaining the highest standard for security.
At Akeyless, our top concern is protecting our customers’ most sensitive information – their secrets; credentials, certificates and encryption keys.
Likewise, Akeyless DFC™ technology is based on standard cryptography and is FIPS 140-2 Certified by the US NIST.
Akeyless is also SOC2 Type2, ISO 27001, and GDPR compliant.