
DevOps | Security
API Keys: How They Secure Your Digital InteractionsIn this blog post, discover how understanding API keys can make your online activities safer and more efficient. Make your online interactions seamless and secure.

DevOps | Security
API Keys: How They Secure Your Digital InteractionsIn this blog post, discover how understanding API keys can make your online activities safer and more efficient. Make your online interactions seamless and secure.

DevOps | Security
Encryption Keys Demystified: The Key to Secure DataIn our latest blog post, we explain the basics of encryption keys and how they protect data. Read on to understand how to improve data security in your digital interactions.

DevOps | Security
What is an SQL Injection Attack?One of today’s most dangerous cybersecurity vulnerabilities is an SQL injection flaw, which can lead to severe consequences if not addressed. This blog will provide an in-depth look at SQL injection flaws, what an SQL injection attack is and most importantly, how to prevent them.

Security
Secrets Management Best Practices: A Comprehensive GuideDiscover secrets management best practices to help you navigate the task of safeguarding sensitive data like passwords, tokens, and API keys.

DevOps | Security
Secrets Management Debt: The Jenga Tower of SecuritySecrets management debt, the compounded burden of overlooked passwords, keys, credentials, and certifications, is like an unbalanced Jenga Tower threatening to collapse at any moment.

DevOps | Security
How the LastPass Breach Highlights the Importance of Secrets ManagementThe LastPass breach marks a turning point in cybersecurity, emphasizing the potential risks of storing sensitive data in password managers and the rising importance of secrets management.
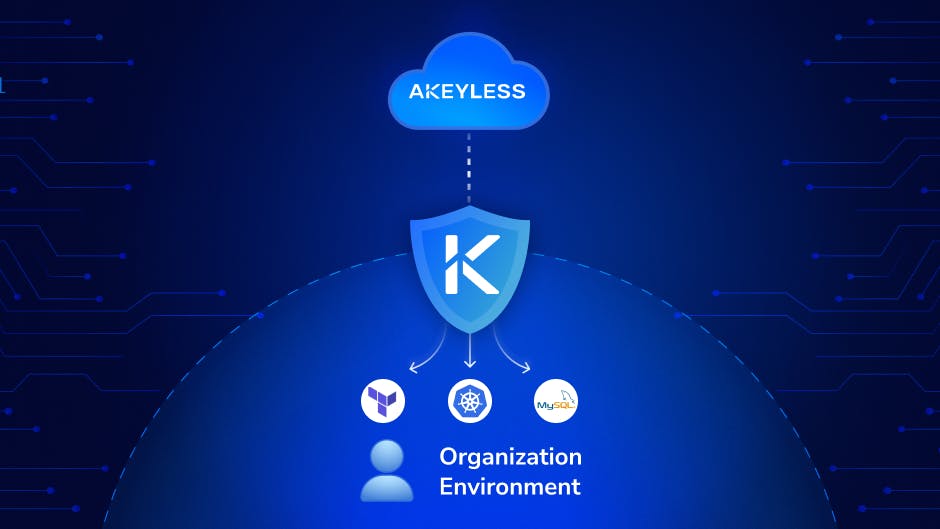
DevOps | Security
How the Akeyless Gateway Protects Your SecretsThe Akeyless gateway serves as protection between your private network and the cloud. Equipped with caching and zero-knowledge encryption capabilities, the Akeyless gateway is the powerhouse of the Akeyless SaaS platform.

DevOps | Security
Using GitHub Securely: Best Practices & What to Watch Out ForDevelopers on public GitHub leak over 5,000 API keys or credentials every day. Learn best practices to avoid credential breaches on GitHub.

Security
5 Dimensions to Securing Machine IdentitiesMachine identities need access to a vast amount of secrets, which need to be securely orchestrated when needed. Let’s look at four ways in which a secrets management solution can help to secure machine identities.
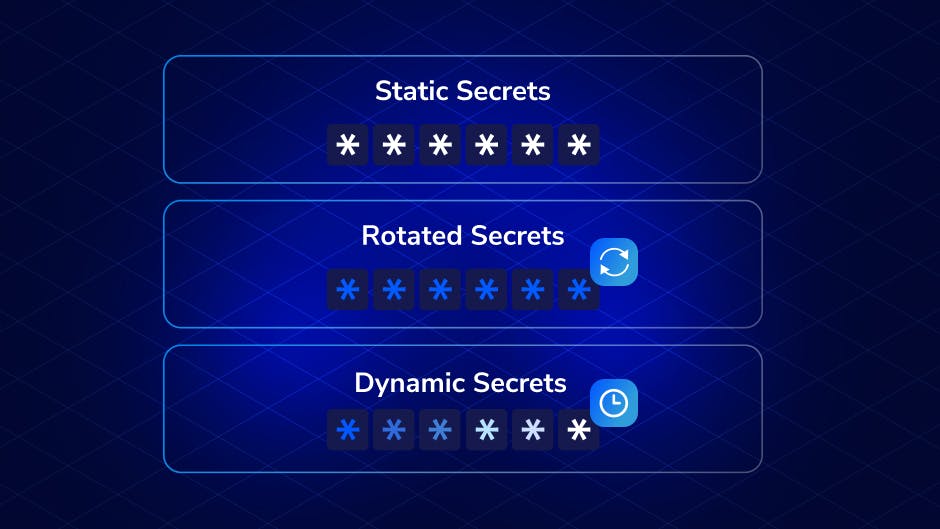
DevOps | Security
What’s in a Secret? Best Practices for Static, Rotated and Dynamic SecretsSecrets are ranked as the leading cause of data breaches. Combat this by learning how to best use static, rotated, and dynamic secrets.

Security
It’s All About Secrets Management: Preventing a SolarWinds Hack in 2023In an era characterized by rapid digital expansion and interconnectivity, cybersecurity threats are more prevalent than ever. Supply chain attacks, in particular, have emerged as a formidable threat to governments, corporations, and individual users alike. The chilling impact of these threats was brought to the fore during the infamous SolarWinds breach. This catastrophe affected around […]

DevOps | Security
Key Ownership in the Cloud: Using Zero Knowledge to Protect Your DataCustomers often wonder if their data is secure in the cloud. To answer this, let's discuss key ownership and zero trust.