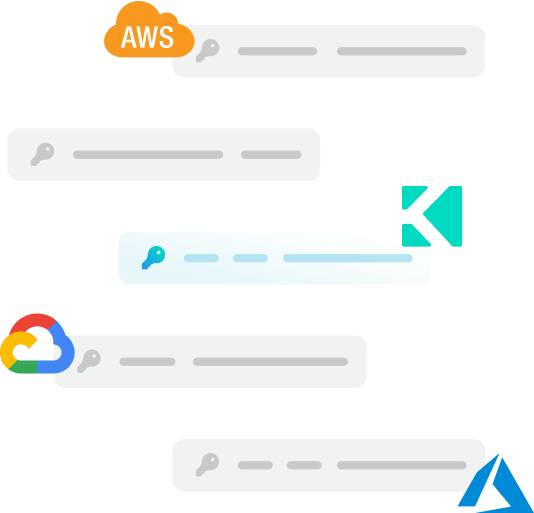
Universal Authentication
Simplify authentication by utilizing external Identity Providers like Okta, AWS IAM, Azure AD, and more
Akeyless unveiled the world’s first Unified Secrets and Machine Identity Platform to address the #1 cause of breaches. Discover Why & How.
Akeyless Vault is your answer! Schedule your 1:1 demo with us today and see why enterprises use Akeyless over HashiCorp Vault.
Let’s have a short chat about your current use case. Maybe we can help 🙂
Simplify authentication by utilizing external Identity Providers like Okta, AWS IAM, Azure AD, and more
Protect any type of secret like connection strings, passwords, tokens and encryption keys with Zero-Trust Encryption
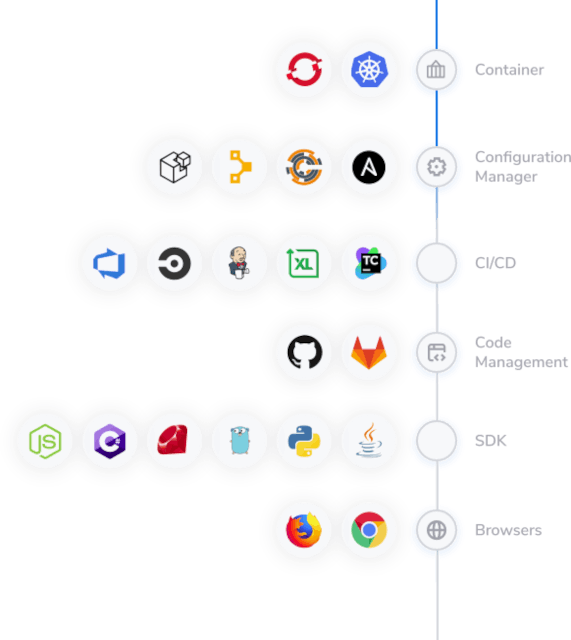
Use various plugins to push secrets into your CI/CD pipelines, Configuration Management, and Container Orchestration tools
Eliminate secret proliferation in code by using various SDKs
Enable humans to also manage secrets via a browser extension, providing quick access to private and teams shared secrets
Simplify authentication by utilizing external Identity Providers like Okta, AWS IAM, Azure AD, and more
Protect any type of secret like connection strings, passwords, tokens and encryption keys with Zero-Trust Encryption
Use various plugins to push secrets into your CI/CD pipelines, Configuration Management, and Container Orchestration tools
Eliminate secret proliferation in code by using various SDKs
Enable humans to also manage secrets via a browser extension, providing quick access to private and teams shared secrets
Segregate access between identities at various levels (i.e. pods, namespaces, playbooks, jobs and more)
Limit machines and users’ access rights, to the minimum they need
Collect detailed audit logs of any operation that was made by either users or machines, together with time-stamped trace
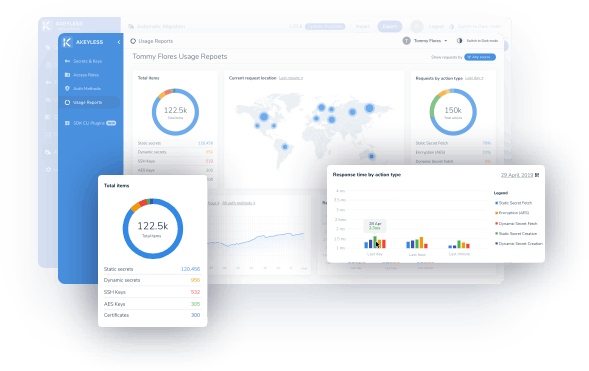
Analyze the status of secrets posture in various environments from a birds eye view
Empower the analysis of your logs by shipping them to a central SIEM or your log management system